We use CSBAuditor, a novel cloud security system that continuously audits Cloud Storage Broker (CSB) resources e.g. CloudRAID, to detect malicious activities and unauthorized changes e.g. bucket policy misconfigurations, and remediates these anomalies. This approach is particularly imperative given the increasing attacks against cloud storage owing to misconfigurations, which have led to several data breaches e.g. the Verizon AWS S3 data breach.
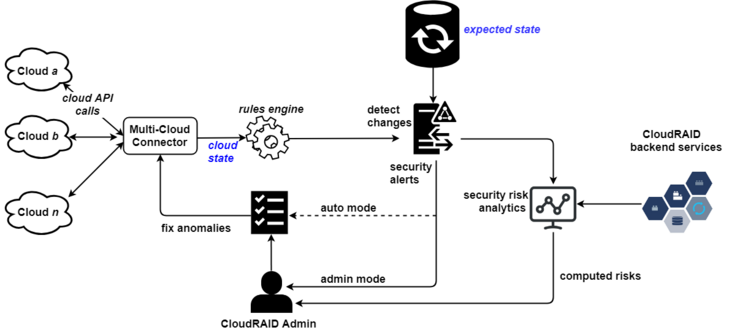
Our methodology consists of consistent maintenance of the cloud state via a continuous snapshotting mechanism thereby ensuring fault tolerance and visibility. We adopt the principles of chaos engineering by integrating BrokerMonkey, a complimentary system that continuously injects failures into our reference CSB system, CloudRAID. Hence, CSBAuditor is continuously tested for its efficiency in detecting unauthorized changes made in the cloud accounts which could indicate cloud attacks. Furthermore, unlike similar systems CSBAuditor employs security metrics for risk analysis by computing numeric severity scores for detected vulnerabilities using several methodologies e.g. the Common Configuration Scoring System. Hence, the limitation of insufficient or binary-based security metrics in existing cloud auditing schemes is overcome and the security of monitored cloud services is quantitatively measured.

