Cyber Security Management (Wintersemester 2021/2022)
Dozent:
Prof. Dr. Christian Dörr
(Cyber Security - Enterprise Security)
Allgemeine Information
- Semesterwochenstunden: 4
- ECTS: 6
- Benotet:
Ja
- Einschreibefrist: 01.10.2021 - 22.10.2021
- Lehrform: Vorlesung / Übung
- Belegungsart: Pflichtmodul
- Lehrsprache: Deutsch
Studiengänge, Modulgruppen & Module
- Cybersecurity
- HPI-CS-T Security Technologies
- HDAS: Health Data Security
- HPI-HDAS-C Concepts and Methods
- HDAS: Health Data Security
- HPI-HDAS-T Technologies and Methods
- HDAS: Health Data Security
- HPI-HDAS-S Specialization
- DSEC: Data Security
- DSEC-Konzepte und Methoden
- DSEC: Data Security
- DSEC-Techniken und Werkzeuge
- DSEC: Data Security
- ISAE: Internet, Security & Algorithm Engineering
- HPI-ISAE-T Techniken und Werkzeuge
- IT-Systems Engineering
- IT-Systems Engineering
Beschreibung
The goal of cybersecurity is to identify cyber risks and reduce them to an acceptable level. From a strategic view, an organization’s cybersecurity program and cyber risk management has to fulfill five core functions. There have to be processes to identify cyber risks, a deployment of safeguards and detection capabilities, as well as organizational and technical measures to respond and recover from a cyber incident.
This course covers the relevant standards, frameworks and best practices to establish a cyber risk management program from a technical, governance, and legal perspective. The lecture is accompanied by a semester-long case study, where you identify and evaluate the cyber risk for an organization, and develop a customized cybersecurity program to treat them. | 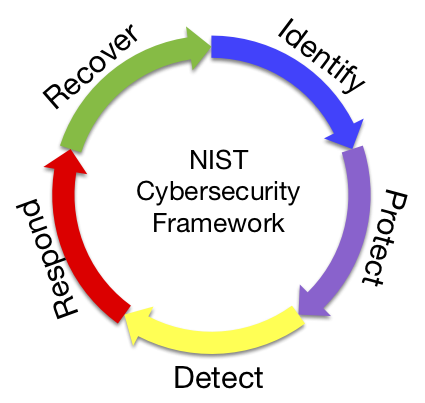 |
Covered topics:
Identify
- Security governance and risk management standards (i.a. ISO31000 series)
- Threat identification, cyber threat intelligence and cyber attack analysis models
- Information Security Management Systems (i.a. ISO27000 series)
- Compliance standards and frameworks
- Risk management frameworks specific to critical infrastructures and select sectors
Protect
- Categorization of controls (technical and non-technical; preventive, detective and responsive controls)
- Security standards (i.a. BSI Grundschutz)
- Security architectures and best practices (least privileges, defense in depth, security by design)
- Physical security, asset and identity management
- Security awareness
Detect
- Logging and monitoring systems
- Security assessment and metrics
Respond
- Vulnerability management
- Triage and threat analysis
- Intelligence-driven incident response
Recover
- Business continuity planning and disaster recovery
- Crisis management and communication
Literatur
Kurswebseite im Moodle XXXXXXXXXXX
Lern- und Lehrformen
Vorlesung und Übung.
Veranstaltung findet in Präsenz statt.
Leistungserfassung
Abschlußklausur, Zulassung zur Klausur mit erfolgreicher Teilnahme an Übungen.
Zurück

